As per this announcement made on Feb 2021, Microsoft graph now provides option to have granular permissions level using Sites.Selected application permission for the AD application instead of granting permission for all the sites in the tenant. The permission Sites.Selected does not provide access to any SharePoint site collections for the application unless the AD application has been assigned with permission roles read or write by an Admin. On this post let us see how to grant a site permission (Read or Write) to an AD Application with Sites.Selected permission by using postman client. As of the time I am writing this post there is no user interface to assign permissions to specific site collections for the application.
Pre-Requisite:
- Register Azure AD Application (APP 1) in Azure AD Portal with the following permissions
- Sites.Selected (Admin Consented)
- Another AD Application (APP 2) with following permission only for the admins to assign selected roles to the above App
- Sites.FullControl.All (Admin Consented)
App Registration:
Start with registering the above said two Azure AD applications
APP 1:
Register an Azure AD application with the following permission
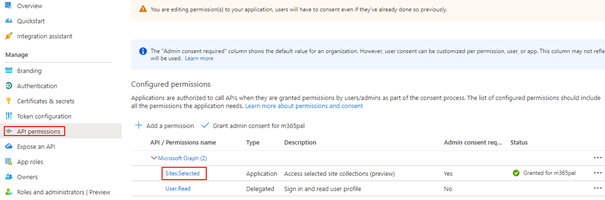
APP 2 (Admin App):
Another app for admins for granting roles to APP 1

Grant permission role to the SharePoint site for the Azure AD Application:
This step is grant permission for the Azure AD application with Sites.Selected application permission to a given site collection. Perform the following steps to grant the role (Read/Write or Read and Write) to the AD app (APP 1)
- Gather the Client ID, Tenant ID and Client secret of the admin app
- In PostMan, make a HTTP request to generate the access token for the admin app – APP 2
Request Method: POST
Request URL: https://login.microsoftonline.com/yourtenantID/oauth2/v2.0/token
Request Header:
Key: Content-Type
Value: application/x-www-form-urlencoded
Request Body:
grant_type: client_credentials
scope: https://graph.microsoft.com/.default
client_id: adminappclientid
client_secret: adminappclientsecret
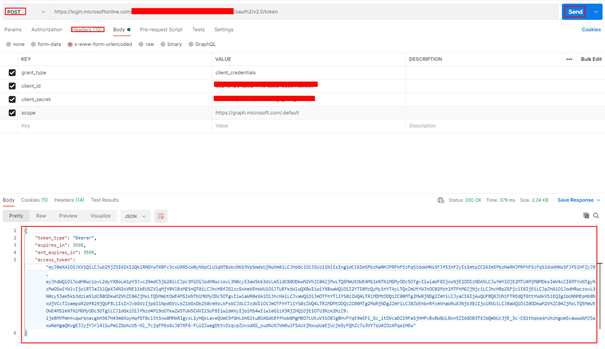
- Copy the access_token to be used for granting roles.
- Get the Client ID of the Azure AD Application – APP 1 with Sites.Selected permission
- Decide on the Role (Read or Write) for the granting the Site specific role for the APP 1 with Sites.Selected permission.
- Get the SiteId of the SharePoint site to be assigned permissions for the application (App 1). An easy way to get the siteId is by viewing the page source from the browser with the site open.
- In PostMan, make a HTTP request to grant the site role to the APP 1. Replace the siteId with the actual siteId which will be a guid
Request Method: POST
Request URL: https://graph.microsoft.com/v1.0/sites/siteId/permissions
Request Header:
Key: Content-Type
Value: application/json
Request Body: raw
Replace the id with APP 1 client id and the display name of the APP 1
{
"roles": ["write"],
"grantedToIdentities": [{
"application": {
"id": "xxxxxx-APP1GUID-4ad9-xxxx-4d36e68b0454",
"displayName": "AppNamewithSelectedPermissions-App1"
}
}]
}
- Paste the access token on the token box as shown below with Authorization type selected as Bearer Token
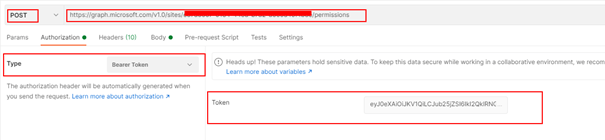
- Send the request for granting the role for APP 1. After the request is made the APP 1 with the Sites.Selected permission has access to the site with write role we have granted to. The same way you can assign app access to multiple SharePoint sites.

Grant the Role using PnP PowerShell:
There is a PnP PowerShell cmdlet to grant access to SharePoint site for the registered AD application with Sites.Selected permission. The command to grant permission can be executed by the Site Collection administrator after creating a connection to the site
Connect-PnPOnline https://tenantname.sharepoint.com/sites/siteName -InteractiveYou will be prompted to enter credentials including the second factor. After the connection is created, enter the following command to grant Write permission to the AD App
Grant-PnPAzureADAppSitePermission -AppId 'AzureAppIdwithSitesdotselectedpermission' -DisplayName 'App Name here' -Site 'https://tenantname.sharepoint.com/sites/sitename' -Permissions Write
To install PnP PowerShell module on the local workstation, enter the following command
Install-Module -Name PnP.PowerShellThere is also a PnP cmdlet to register an AD app in the Azure Active directory.
Grant the Role by an Admin using the Graph Explorer tool:
Role can also be assigned by an admin with out having the admin AD app (APP 2) using the graph explorer tool. This can be done only by an Admin

If there is any error related to permissions, make sure the admin consents to Sites.FullControl.All for the Graph tool. There is also an SPFx community webpart developed by a community member with User Interface for this operation
https://github.com/pnp/sp-dev-fx-webparts/tree/master/samples/react-sites-selected-admin
Reference:
Assign permission role programmatically: https://docs.microsoft.com/en-us/graph/api/site-post-permissions?view=graph-rest-1.0&tabs=csharp
Summary:
On this post we have seen how to grant access to Azure AD which has the Sites.Selected permission. You can also grant permission/role to an app with sites.selected permission programmatically. If you are using SharePoint API instead of Graph API in the Azure AD app registration, Sites.Selected is available on Application Permission as shown below

Hope you have found this informational & thanks for reading. If you are visiting my blog for the first time, please do look at my other blogposts.
Do you like this article?
Subscribe to my blog with your email address using the widget on the right side or on the bottom of this page to have new articles sent directly to your inbox the moment I publish them.
Hello Mohamed,
Have you try with the APP1 (with Sites.Selected permission) download files or create a new upload session?
Regards
Joel
LikeLiked by 1 person
It should work, I have tested today downloading files from a Document Library with the following API request using APP1 token
To GET Drive Id (Document Library Id) from a SharePoint site: https://graph.microsoft.com/v1.0/sites/siteId/drives
To Get the Download link URL of a file: https://graph.microsoft.com/v1.0/sites/siteId/drives/driveidfrompreviousrequest(libraryID)/root:/filenamewithextension
To get All files from a document library: https://graph.microsoft.com/v1.0/sites/siteId/drives/driveidfrompreviousrequest(libraryID)/root/children
Site ID: https://graph.microsoft.com/v1.0/sites/{host-name}:/{server-relative-path}
https://graph.microsoft.com/v1.0/sites/yourM365DomainName.sharepoint.com:/sites/spSiteName
Reference:
https://docs.microsoft.com/en-us/graph/api/driveitem-get?view=graph-rest-1.0&tabs=http
https://docs.microsoft.com/en-us/graph/api/resources/sharepoint?view=graph-rest-1.0
If the App has Write role assigned, it should be able to upload files as well
LikeLike
In my case the download Url is generated but when I try to download appears the access denied message 😦
{“error”:{“code”:”accessDenied”,”message”:”Access denied”}}
I’ve tried with an app with Sites.FullControl.All and it works.
LikeLike
I got the same issue as Joel Teixeira.
LikeLiked by 1 person
It seems that there’s a bug.
Mohamed, could you please try to download a file using only Sites.Selected permissions?
I was granted with ‘read’ role by an admin that used his admin app – I can browse through the selected site, but cannot download files.
LikeLiked by 2 people
I am trying to use MS Graph with SharePoint sites.selected on a specific site to find files using all or part of a filename. I found this to work with Sites.FullControl.All, but with Sites Selected it does not work. If I add other Sites.* permissions to the App then it grants the access to all sites in the tenant. An example of the GET that I doing is as follows: https://graph.microsoft.com/v1.0/sites/{SiteID}/drive/root:/upload:/search(q=’water1001′)
Is there any other way to find a file by all or part of the name just using sites.selected and without granting the app permissions to other sites?
LikeLike
I am too getting access denied error for file downloads but it worked last week. Though able to create list items. Will post updates here as soon as I have some regarding the error. Thanks
LikeLiked by 1 person
Hi, Thanks for the post, it is really interesting! We were going to test the feature, since we are receiving this kind of requests. However, due to the fact is still in preview and it seems there could be bugs…, do you recommend wait a while until Microsoft confirms the feature is reliable?
LikeLiked by 1 person
Hey David! Thanks for reading the post, yes it a much sought after feature. As far as I have tested, it has few issues when comes downloading files from SharePoint libraries. These issues has been brought to Microsoft product teams attention. I recommend you to wait until it is generally available. Please do take a look at the roadmap for this feature
https://www.microsoft.com/en-us/microsoft-365/roadmap?filters=&searchterms=Sites.selected
LikeLiked by 1 person
Hi Mohamed
> These issues has been brought to Microsoft product teams attention.
Where can I find that the Microsoft product teams are working on this? The details on the roadmap are unfortunately sparse.
LikeLike
Hi Jenny!
Agreed. I did raise a support request couple of months back, after investigation they have closed the request stating that the feature is still in development & the issue has been brought to product teams attention. The only channel available is the Road Map link or by contacting Microsoft support Team.
LikeLike
Thanks for the informative article, Mohamed. I’ve been testing this feature and for me here’s what my app can do with the read+write permissions for a selected site
– read and create folders
– list, upload, and download files
And what it can’t do for the selected site
– create lists, such as document libraries
Going to be keenly checking that roadmap you linked above. Thanks!
LikeLiked by 1 person
Thanks for the comment Jenny!
LikeLike
Thanks for the feedback Sridhar!!
LikeLike
Thanks Jenny!
LikeLike
Hi Jenny,
To create lists and Doc Libraries you need to set the permission fullcontrol to your app in the site.
Regards
LikeLike
I was worried that’d be the case 😦 Thanks for the comment, Joel
LikeLike
But doing that you give you app FullControl over all sites of the tenant. it’s too much rights in my case.
LikeLiked by 1 person
Hello Laurent!
With Sites.Selected permission, it will not give access to all sites, you will get it only to the site which you have granted for which can only be either Read or Write.
LikeLike
For some reason I can’t reply to comments that are nested 2 levels deep.
Hi Mohamed,
I think what Laurent meant is that if we’re using Sites.Selected and then add Sites.FullControl.All on top of that, it’ll render the Sites.Selected app permission useless because we’re now having full control over all sites of the tenant. Because I can now create lists and doc libraries for my selected site AND any other site in the tenant too, which is not what my enterprise customer wants to allow me to do.
LikeLike
Hi ! How do you set the FULL CONTROL permissions on the Site object ? I can only set Read or Write. I tried Manage, FullControl and even Owner, i still get an “Invalid value for role” error.
I haven’t found any documentation for other roles, and the PnP powershell cmdlet only accepts Read or Write too.
LikeLike
Hi Jonathan,
This isn’t documented.
You need Create first the permission, you can use read or write and after patch the role as fullcontrol
Method: PATCH
URI: https://graph.microsoft.com/v1.0/sites/{SiteID}/permissions/{PermissionID}
Body:
{
“roles”: [
“fullcontrol”
]
}
LikeLike
Hi Mohamed Ashiq Faleel,
Thank you for this informative article. Permission from Postman/Powershell is not getting applied to site after successfully running above instruction. Is there any issue at microsoft end with APIs/commands?
Regards,
Pratik
LikeLike
Thank you for this post. Worked great for assigning permissions to a SharePoint in North America. I have a SharePoint site hosted in the EMEA Region, and I get an “Item not found” error trying to set the permissions in PostMan. IE. Instead of https://mycompany.sharepoint.com, the site URL begins with https://mycompanyemea.sharepoint.com. Does the the EMEA region have limitations?
LikeLike
It should work irrespective of region, no location specific limitations. If there is an active M365tenant mycompanyemea, then I don’t see any issue.
LikeLike
Thanks man, awesome post! Just a quick question, because I’m not really sure if it is possible to look it up, but is there a way to see which sites are all selected/allowed by Sites.Selected?
LikeLike
you’d need an app with access to all sites, collect all site IDs and then use it to cycle through all your sites via API and parse the results of this endpoint
https://graph.microsoft.com/v1.0/sites/{site id}/permissions
LikeLike
Thank you – this really helped – great stuff
LikeLiked by 1 person
Thank you for sharing! I have been read/write using PowerShell successfully with Microsoft new feature Sites.Selected using two AAD registered apps, Admin and Client.
I would like to do the same in a C# program but get access denied using Sites.Selected.
Here is the short video with an example of the new Sites.Selected Microsoft feature using MS Graph (no certificates) and SharePoint CSOM (with certificates):
Episode #200 – Sites.Selected Application permission for Graph and SharePoint APIs – YouTube
It would be great if you could provide a post on the Sites.Selected permission with a C# app that read/write to Sharepoint using MS Graph. Thank you! Respectfully, Juan
LikeLike
Good Post!
I too been trying very long with “SharePoint/Sites.Selected”, but it is denying access while reading a File with in that permitted site collections (even though I have set Full control for my app id in SharePoint online). I can get authorized until Sites, Document root folder, but while reading a file within the site collections, its denied.
I am using CSOM libraries in my C# project for this assignment. Appreciate on any help provided. Thanks,
Jia
LikeLike
Thanks for sharing the wonderful article.
One question- can we assign multiple site collection to single AAD (generated for sharepoint–> sites.selected)?
LikeLike
Hello Mohamed,
Thanks for the tutorial.
It worked well for the environment I am working in , where I had to assign custom permission to an App registration for some specified SharePoint online sites.
Is there a way to view , with whatever tool, the assigned roles that an App reg. has on specified SharePoint online sites?
LikeLike
We can no longer use interactive login with PNP. Need to use an app registration with sites.all.read to connect, then can assign sites.selected as before. See this article:
LikeLike